Streaming under Siege: Defending Online Media in a Growing Threat Landscape
With their valuable content, sensitive data, and wide reach, online broadcasters are prime targets for cyberattacks. Threats include DDoS attacks, credential stuffing, and piracy, often motivated by financial gain or political agendas.
On this page
Introduction
The increasing accessibility of hacking tools and techniques continues to fuel the rise of online security threats. Organizations face a constant influx of diverse threats, ranging from ransomware and phishing to credential stuffing and distributed denial-of-service (DDoS) attacks, and from their inception, online media companies have found themselves prime and constant targets. This report looks at the current threat landscape as it pertains to streaming media and will also recommend actions the industry must take to fight off ill-intended actors.
An Industry attacked from all sides
For years, online broadcasters have been highly vulnerable to cyberattacks due to the valuable content they host, the broad reach of their platforms, and the significant financial stakes involved. Streaming platforms and broadcasters manage large amounts of sensitive data, including user information, payment details, and content rights. This makes them appealing to hackers who aim to steal, ransom, or monetize such data.
Cybercriminals also target broadcasters to disrupt services through DDoS attacks, which can cause significant revenue losses during high-profile events. Disruptions can damage a broadcaster’s reputation and customer trust. Additionally, broadcasters face constant risks from credential stuffing attacks, where stolen credentials are used to gain unauthorized access to accounts, leading to account takeovers.
Live news outlets that express specific viewpoints also face cyberattacks intended to silence or disrupt their operations. State-sponsored actors or independent hacktivist groups can carry out these attacks with the goal of serving political agendas or retaliating against perceived bias. As the media's influence on public discourse continues to grow, it becomes an increasingly prominent target in the cyber landscape.
Finally, content is highly valuable. Particularly attractive are early-release films or live events, which garner widespread attention and are profitable targets for piracy. As streaming platforms expand and carry more content, they face persistent security challenges, such as password sharing, which many platforms have begun addressing with stricter policies and options like paid-sharing models.
The above clearly shows that as an industry, streaming media requires strong security measures to safeguard editorial integrity, data and assets, reputation, and its often complex digital infrastructure.
Online attacks are on the rise
This month we released our latest version of Fastly’s Threat Insights Report, which found that 91% of cyberattacks – up from 69% in 2023 – targeted multiple customers using mass scanning techniques to uncover and exploit software vulnerabilities. The data reveals an alarming trend in attacks spreading throughout a broader target base and provides insight into the latest attack trends and techniques across the web application and API security landscape.
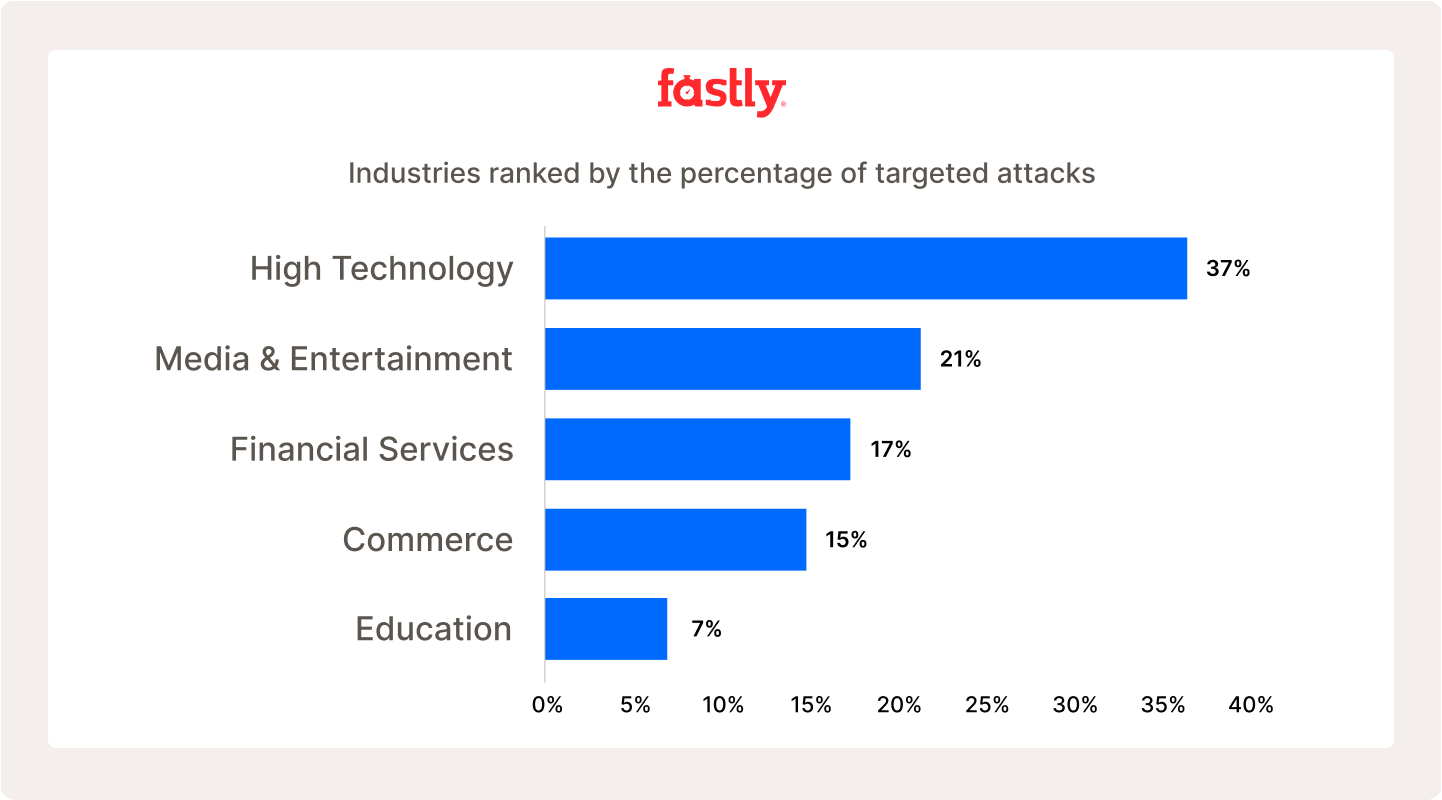
As an industry, Media & Entertainment saw the second-most attacks (21%). Only High Tech saw a higher number of attacks, which can likely be attributed to the broader impact a successful breach in this industry would have on many, if not all, customers using the services. The data also showed that attackers no longer target just one company. 19% of the specific attacks Fastly tracked targeted more than 100 customers simultaneously!
The efficacy of NLX improves as our network grows, allowing Fastly to observe a larger traffic volume and analyze attacker behavior more comprehensively.
The above findings are based on security data collected from April 11 to June 30, 2024, from Fastly’s Network Learning Exchange (NLX), the collective threat intelligence feed for Fastly’s Next-Gen WAF. They have previously been reported in the Fastly Threat Insights Report.
How a CDN can help
A CDN can greatly enhance your defense against online attacks. Acting as a shield between an application’s origin server and online threats, it can mitigate various attacks, especially DDoS attacks. When an attacker attempts to overwhelm a website with an influx of traffic, a CDN, given its massive size, can absorb and disperse the malicious traffic across its globally distributed network of servers. By spreading the load, the CDN reduces the strain on the origin server and prevents it from crashing, thus ensuring legitimate users can still access the site.
In addition to DDoS mitigation, CDNs provide enhanced protection against online attacks, such as web application exploits and bot activity. Many CDNs can integrate web application firewalls (WAF) that inspect incoming requests and filter out malicious traffic before it reaches the origin server. WAFs can block SQL injection attempts, cross-site scripting (XSS), and other common vulnerabilities that hackers often exploit. Moreover, some WAFs have built-in bot management systems that distinguish legitimate users from harmful bots, reducing the risk of credential stuffing, scraping, and other automated threats.
By adding the scale and capacity of a CDN, organizations can enhance the resilience and performance of their web applications while maintaining a secure online presence. Visit our dedicated DDoS Protection page for more information on one of Fastly’s online security solutions.
Case study: Forensic Watermarking a possible solution to piracy
Forensic watermarking is a technique used to embed invisible markers into video, audio, or images. This allows content owners to trace unauthorized copies back to their source. Unlike traditional watermarks, forensic watermarks are not visible to viewers and can withstand common forms of tampering like re-encoding, cropping, or compression.
The technology works by embedding data within the content itself, such as identifying information or unique codes associated with specific users or distribution channels. If pirated content appears online, the embedded watermark can be extracted and analyzed to determine the source of the breach, helping content owners take legal action or improve security.
Although adoption is still in the early stages, forensic watermarking in streaming media is increasingly used to safeguard high-value content, especially during early-release windows when the risk of piracy is high. It can be integrated into both live and on-demand streams and deployed alongside real-time monitoring systems to detect leaks quickly. This approach provides a strong deterrent against piracy by holding those responsible for breaches accountable.
Rethink your security approach
When it comes to streaming media, traditional security methods like firewalls and encryption remain crucial. They need to be integrated into an architecture that supports agility and scalability. Given their central infrastructure placement, modern security strategies increasingly rely on adaptive tools that can dynamically respond to threats in real time.
Due to the highly competitive online entertainment market, it’s essential that these advanced defenses be implemented without creating friction that slows down online experiences, such as excessive authentication steps or traffic filtering causing latency. The key lies in a well-architected security framework that is proactive, flexible, and user-centric, ensuring that security is effective without becoming a hindrance.
This is where next-generation WAFs come in. Unlike their predecessors, modern WAFs use advanced technologies such as machine learning, behavioral analysis, and real-time threat intelligence to detect and mitigate attacks as they occur. They provide customized protection to identify and block malicious traffic without disrupting legitimate users, ensuring a smoother and more secure streaming experience.
For streamers, investing in strong security measures isn't just about preventing disruptions; it’s about protecting their brand, maintaining audience trust, and ensuring uninterrupted engagement. By understanding the threats they face and the available solutions, online content creators can better protect themselves and focus on what truly matters: delivering high-quality content to their audiences.
Related resources
Many CDNs offer the same types of services, but they're not all the same. Whether you're trying to improve your performance and security, or selecting a CDN to start with, use this guide to distinguish the best from the rest.
Choosing the wrong WAF can lead to high false positives, brittle AppSec configurations and high maintenance costs. That’s why having the right evaluation criteria is essential.
Evaluate edge cloud platforms, to make the best choice for your enterprise needs
See how Fastly is helping leading online media brands deliver engaging viewer experiences
Meet a more powerful global network.
Our network is all about greater efficiency. With our strategically placed points of presence (POPs), you can scale on-demand and deliver seamlessly during major events and traffic spikes. Get the peace of mind that comes with truly reliable performance — wherever users may be browsing, watching, shopping, or doing business.
497 Tbps
Edge network capacity1
150 ms
Mean purge time with Instant Purge™
>1.8 trillion
Daily requests served4
~90% of customers
Run Next-Gen WAF in blocking mode3
As of December 31, 2024
As of December 31, 2022
As of March, 2023
As of July 31, 2023
Support plans
Fastly offers several support plans to meet your needs: standard, gold and enterprise.
Standard
Free of charge and available as soon as you sign up with Fastly.
Gold
Proactive alerts for high-impact events, expedited 24/7 incident response times, and a 100% uptime Service Level Agreement (SLA) guarantee.
Enterprise
Gives you the added benefits of emergency escalation for support cases and 24/7 responses for inquiries (not just incidents).